Published Jun 14, 2023 by Xiph
Anyone who’s ever been to a beach will know − sand gets everywhere. It’s the same deal when you code and use programs and web applications that can interfere with the rest of your operating system. Pairing programs or having various developers write code can get messy quickly, putting your operating system and devices at risk. Add potentially risky programs, misconfigured files, or code and things get downright dirty. That’s where sandboxing comes in.

What is sandboxing?
In the context of cyber security, sandboxing is an isolated test environment on a network that mimics end-user operating environments. Sandboxes run separately from your computer and your network to inspect and run untested or suspicious programs or code from unverified third parties, suppliers, users, or websites, without risking harm to your device or operating system.
Isolated test environments function like a ‘sandbox’ that allows developers to play with different variables on separate running programs to find errors or security issues and mitigate system failures or software vulnerabilities from spreading to other areas of the computer or network. You can also liken it to quarantine for unknown code and web resources.
Like a physical sandbox at a playground where kids can create sandcastles and anything they want within the boundary without making a mess elsewhere, sandboxing provides a fully isolated and controlled environment to execute all types of code, applications, and programs without contact with the external environment.
How does sandboxing work?
Sandboxing isolates code execution and coding script to a virtual testing environment independent of your surrounding infrastructure. This is where you can run malicious code, suspicious programs/files, viruses, or other malware to understand how they work without impacting your organisation's critical IT infrastructure. The way a sandbox functions depends on what is being tested, and you can create multiple sandbox versions to test various techniques. A sandbox can have both software and hardware components.
Sandboxing can take different forms and can be used for quality assurance testing, demonstrations, enhancing collaboration with remote teams, testing new features, and deploying environments at scale.
Sandbox examples in use
Most software and applications use sandboxes by default to protect local operating systems and other resources that run on those systems. Browsers like Google Chrome, Safari, and Firefox have their own sandboxes to separate malicious applications that run on the web from accessing devices. Even programming languages such as JavaScript and Python have their own sandbox to protect local resources from untrusted code.
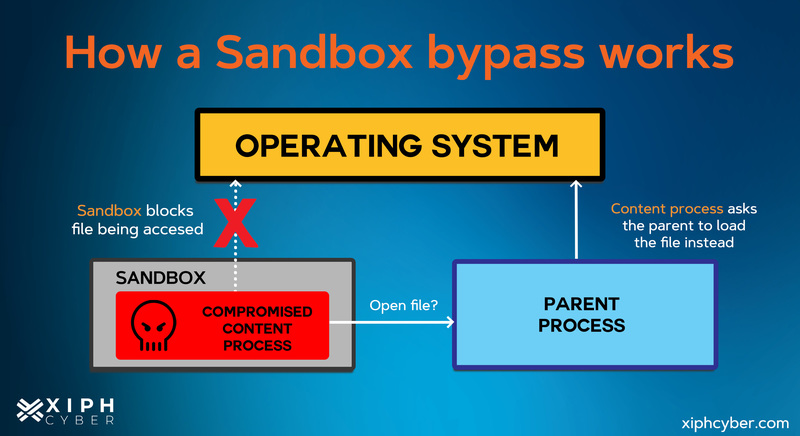
Sandboxing methods
Here are some common sandbox techniques and how they work:
Sandboxing program: Isolates a program on your system or hard drive with tightly controlled or pre-allocated resources including memory space and file systems. You can configure your system to sandbox an application that otherwise would have full access to your system.
Sandbox in the OS: Provides a desktop environment to safely run applications in isolation without impacting the host machine or computer operating system whether that’s your Microsoft Windows, macOS, or any other. Software and applications installed inside the operating system environment remain sandboxed. The Windows 10 operating system has a built-in sandbox called Windows Sandbox and each iOS application runs in its own sandbox.
Web browser sandbox: Runs web applications in isolated environments to prevent browser-based malware from spreading to the network.
Virtual machine: Creates an isolated and temporary virtual machine to test code, upload files, download URLs, and run programs/applications without affecting your core operating system environment. The guest operating system runs sandboxed in the sense that it does not function natively on the host and can only access host resources through the emulator.
Plug-in sandbox: Allows plug-ins and event plug-ins to run in a separate environment. Each plug-in instance can modify its environment without affecting any future instances of the same or other plug-ins.
Benefits of sandboxing
The main advantages of sandboxing include:
- It can safely execute suspicious code with no risk to the host device or operating system. The isolated testing environment mimics the end-user operating environment.
- You can test new code or software updates to see how they behave with different prompts and scenarios before public release. A code analysis virtual environment allows you to test any software update for possible risks before going live. This is an important part of application security.
- It can assess potentially malicious software for threats. This helps when working with new vendors or unknown software sources. You can test new software or applications for threats before implementing them.
- It can quarantine zero-day threats that exploit unknown security flaws.
- It complements other security programs, like anti-virus software, and malware protection.
- Sandboxing has the highest possible threat detection rate.
- It can deploy an application and invite remote teams and various departments to undertake testing in the same sandbox.
- It can be time and cost-effective as it removes the need for a dedicated virtual machine or a secondary device to test code, software, programs, etc.
A final word
Sandboxing is a great way to test programs, identify software flaws, and analyse malware without damaging business-critical resources and infrastructure. It can also detect sophisticated zero-day threats and stealth attacks. For more tips on sandboxing and how to enhance your cyber security, contact us via email: enquiries@xiphcyber.com.
Posted in: Security


